Skip to main contentThis page provides infrastructure diagrams for TextLayer Core.
System Architecture
Overview of the TextLayer Core system architecture.
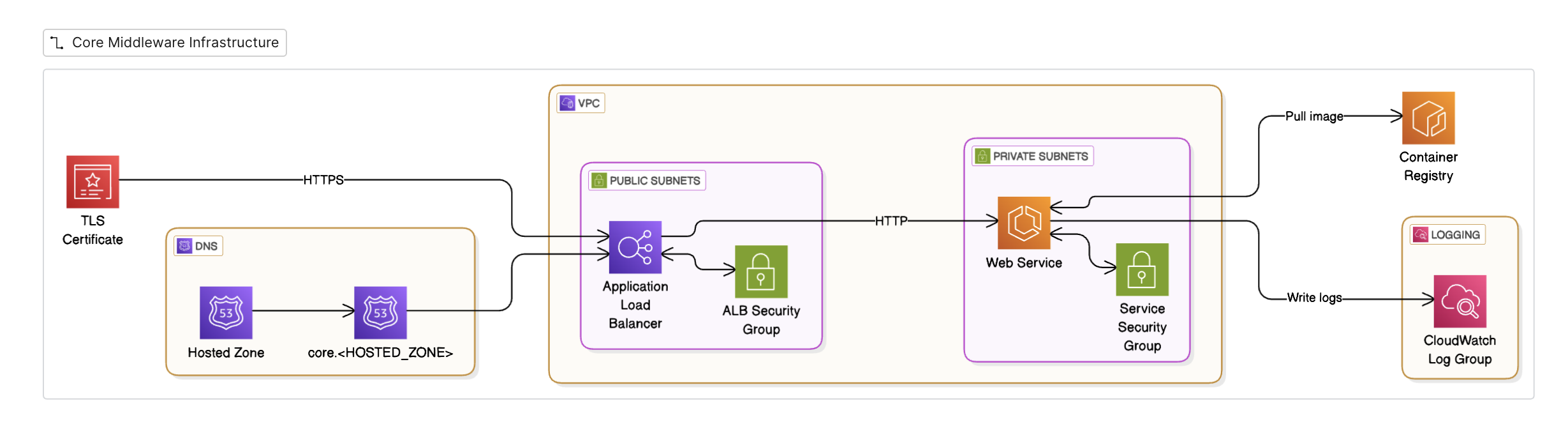
Core Middleware Infrastructure
The Core Middleware Infrastructure diagram illustrates the AWS-based deployment architecture for TextLayer Core.
Key Components
TLS Certificate
- Provides secure HTTPS connections to the application
- Encrypts data in transit between clients and the application
- Managed through AWS Certificate Manager
DNS Configuration
- Hosted Zone: Manages DNS records for the domain
- Core Hosted Zone: Specific DNS configuration for the core middleware services
- Routes external traffic to the appropriate AWS services
Network Architecture
- VPC (Virtual Private Cloud): Isolated network environment for TextLayer Core resources
- Subnets:
- Public Subnets: Host internet-facing resources like the Application Load Balancer
- Private Subnets: Host protected resources like the Web Service, providing an additional security layer
Security Components
- ALB Security Group: Controls traffic to and from the Application Load Balancer
- Service Security Group: Governs access to the Web Service, allowing only necessary connections
Application Components
- Application Load Balancer: Distributes incoming traffic across multiple targets for improved availability
- Web Service: Core application service running in containers within the private subnet
- Container Registry: Stores and manages Docker container images used by the Web Service
Monitoring and Logging
- CloudWatch Log Group: Centralized logging solution for application and infrastructure logs
- Enables monitoring, alerting, and troubleshooting of the entire stack
Data Flow
- External requests reach the system through HTTPS, secured by TLS certificates
- DNS routes the traffic to the Application Load Balancer in the public subnet
- The ALB forwards requests to the Web Service running in the private subnet
- The Web Service pulls container images from the Container Registry when needed
- All components write logs to CloudWatch for monitoring and troubleshooting
This infrastructure follows AWS best practices for security, scalability, and reliability, implementing defense-in-depth through multiple security layers including network segregation, security groups, and private subnets.
Network Topology
Details about the network topology of TextLayer Core.
Security Zones
Information about security zones in the infrastructure. 

